
Maestro+
The security of an online account depends not only on that account's protection strength, but also on the dependencies between the different accounts that a user has.
Context
Real life attacks confirm that accessing somebody else's account by using a secondary account, calling a customer service center or answering a security question is often much easier and less time consuming than cracking the actual account's password.
Dictionary
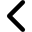
Account access graph
Graphical representation of a user account ecosystem.
Features
Maestro+ is an account manager, new version of Maestro. The objectives of the software are the following : identifing the attacks that the user's account ecosystem is potentially subject to, Analyzing the user's account ecosystem under risk and creating intuitive interface for access graphs. Application is based on research-article "User Account Access Graphs", written by Sven Hammann, Saša Radomirović, Ralf Sasse, David Basin. The main features of Maestro+ are :Dynamic account access graph
Security analysis
- Automatic scan
- Displaying warnings
- Warning menu
Analyzing under attacker profiles


Team
Maestro+ is developed by 4th year students at INSA Rennes.
Jérémy Brunet
Communications manager
Sulaymane Dagnet
Project management manager
Léa Griffon
Project manager
Augustin Lavandier
Reports manager
Lucas Lopez
Git manager
Luka Rakviashvili
Web developer
Barbara Fila
Supervisor
Saša Radomirović
Supervisor



