Vulnerabilities and access graph
To evaluate the security of an account ecosystem we need to understand how they are
built. M. Radomirović, researcher in information security at University of
Surrey (UK) and client of the project, leads a study on the topic and
elaborated a tool with collaborators : access graphs.
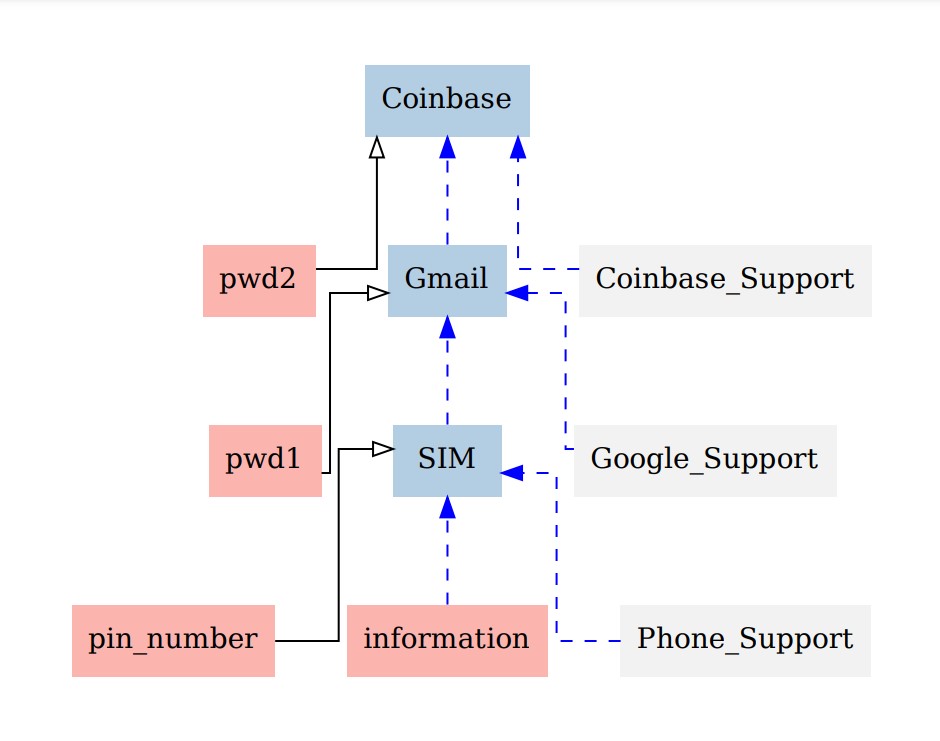
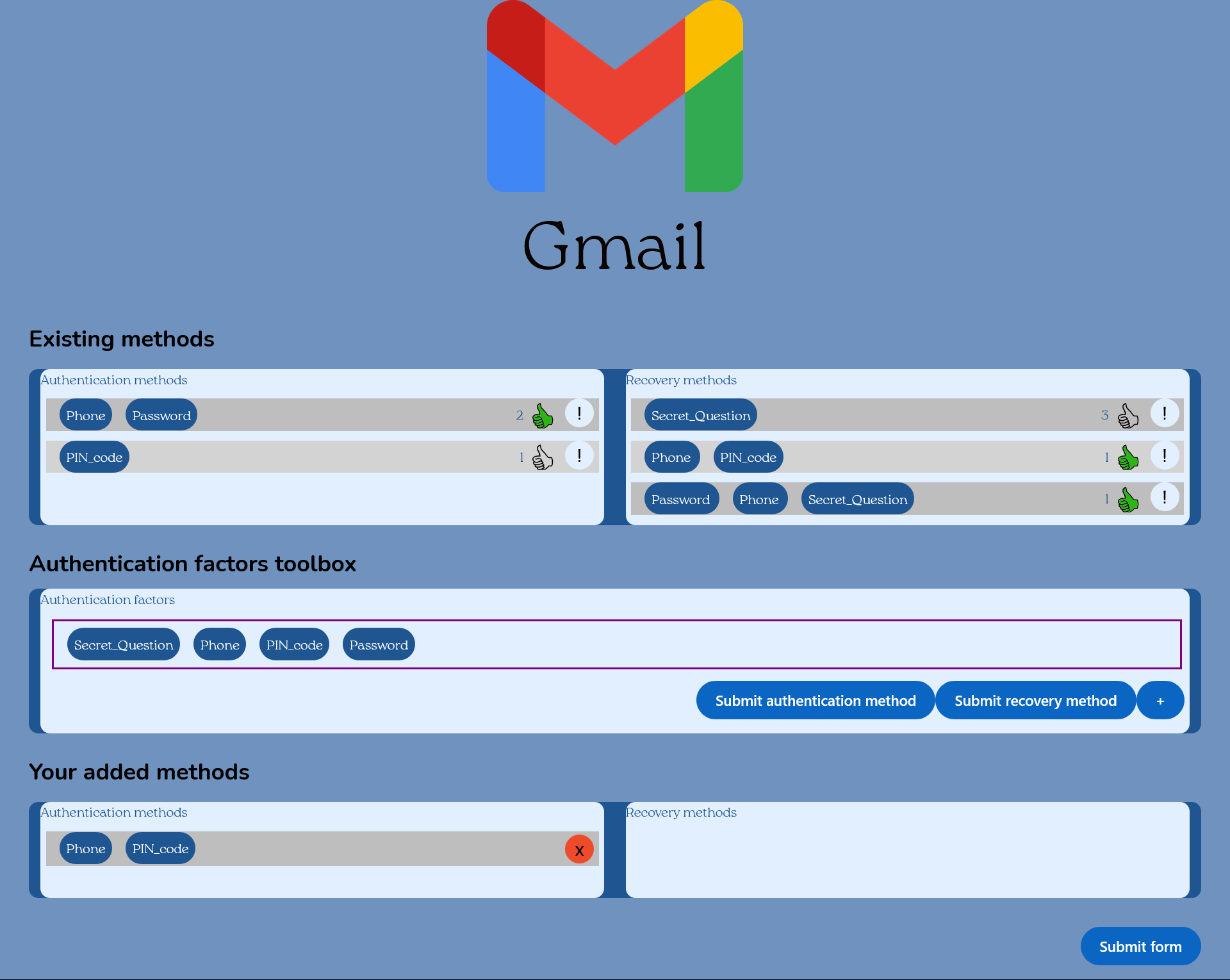
It's a graphical formalism used to represent and analyze account ecosystems. It's composed of authentication factors and platforms (websites or application using account system, for example Facebook) as vertices that are linked with colored edges (a platform can be used as authentication factor).
For a given platform, incident plain edges represent authentication methods and indident dashed edges are recovery methods. To read a method, every authentication factor linked to an incident edge of the same color must be combined.