How to use it?
The time-memory trade-off technique separates the work into two phases:
- The offline phase
- The online phase
The offline phase
It is a pre-calculation phase that generates tables, here rainbow tables, optimizes them and finally exports them. This application is executable and distributable on GPU.
A rainbow table is a data structure that allows to find a password from its hash.
A rainbow table is created by generating chains. To create a chain, we start from a password which will be hashed then this hash will be reduced with a reduction function. We continue the construction of the chain by doing a hash and a reduction on the new password. At the end, the table will keep only the list of couples (starting point, ending point) of the chains, where the starting points and the ending points are plain text passwords.

The application of the offline phase is used on the command line and is configurable, in order to manage the number of chains in a table and the number of tables that we want. This application is intended to be executed on a cluster like Grid'5000, Grid'5000 being a network of machines dedicated to distributed computing and experiments.
./generateTable c mt (startpath) (endpath)- c is the length of a password (in characters)
- mt is the number of ending points in the table (50,000,000 for example)
- (optional) startpath is the path to the starting point file that will be created
- (optional) endpath is the path to the ending point file that will be created
This will create two separate files at the specified paths. These files contain the filtered start and end points, i.e. without duplicates.
The online phase
It is the attack phase that allows the loading of rainbow tables in memory in order to search for the password corresponding to a given hash. This application associated with a graphical interface allows the user to search for a password from a hash in a playful way. it also allows the user to have access to analysis reports on the memory used by the tables, the time of generation of these tables or the time of search of the password.
The online phase is accompanied by a graphical interface. The user must enter one or more password hashes in the search bar, and the interface will run the online phase software in order to find the password that matches the given hash.
Here is an overview of the graphical interface:
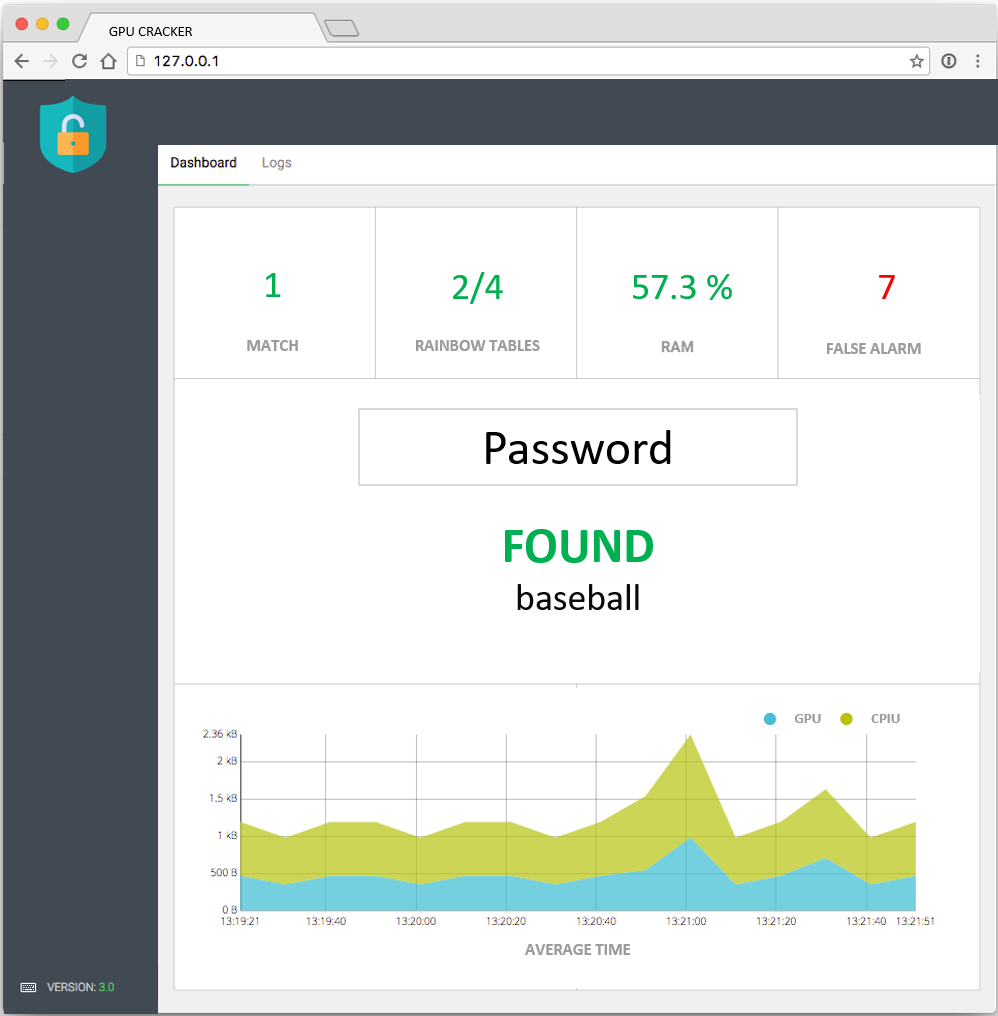
The offline phase is run only once and takes a considerable amount of time, whereas the online phase allows for mass password cracking in a very short time.